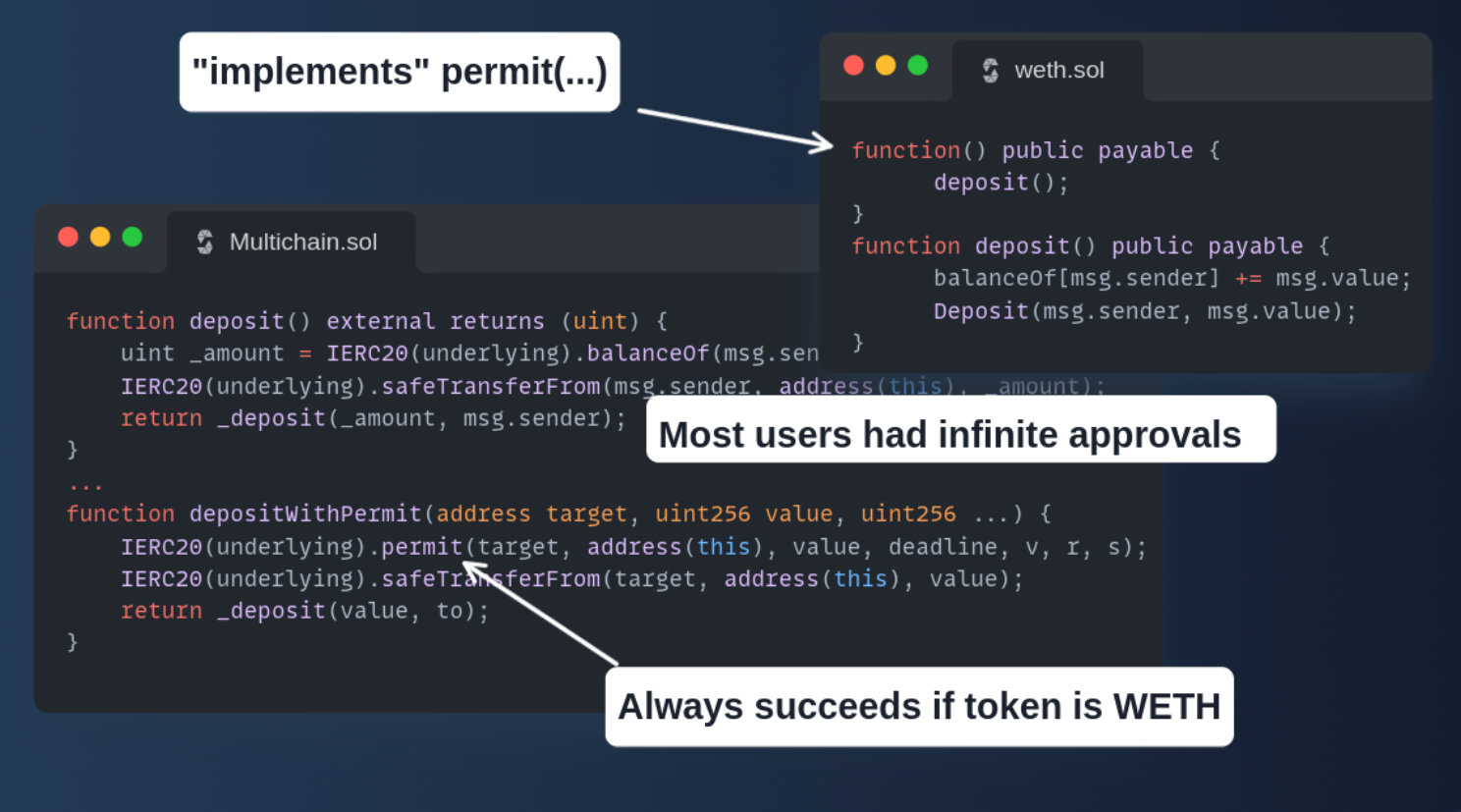
The Dedaub team disclosed a major vulnerability in the Multichain project, primarily affecting Fantom users funds. Had the vulnerability been executed on-chain, it would have resulted in the most significant hack in the history of blockchain technology, with an impact possibly reaching the billion-dollar range. The team discovered two major vulnerabilities in Multichain's contracts. One was in the WETH ("Wrapped ETH") liquidity vault contract, and the other was in the router contract that forwards tokens to other chains. These vulnerabilities had implications not only on the Ethereum network but also on other blockchains like Polygon, BSC, Avalanche, and Fantom. Dedaub's findings led to a public announcement by Multichain, focusing on client impact and mitigation strategies. The vulnerabilities were particularly concerning due to the enormous threat they posed: on Ethereum alone, $431 million in WETH could be stolen in a single transaction from just three victim accounts.
The attack vector was based on what Dedaub termed "phantom functions," specifically related to the token.permit(...) function. In essence, tokens that either don't implement the permit function or have a non-reverting fallback function never cause this function to revert. This means that the call goes through but does nothing ("no-op"), leading to potential security lapses. Most notably, WETH, the ERC-20 representation of ETH, is one such token with this phantom permit. The issue lies in that while clients think they are secure by approving transactions only when they initiate them, the vulnerability allows an attacker to deposit funds belonging to someone else, given that the phantom permit call doesn't fail. For their discovery, the Dedaub team was awarded Multichain’s maximum published bug bounty of $1 million for each of the two vulnerability disclosures.
Read more